In today’s interconnected world, our phones have become extensions of ourselves, holding vast amounts of personal and sensitive information. From banking details and private conversations to personal photos and location data, the potential consequences of a phone hack can be devastating. Therefore, understanding how to protect your phone from hackers is paramount. This article will provide practical steps and security measures you can implement to fortify your phone’s defenses and safeguard your data from falling into the wrong hands. Learn how to identify potential threats, implement strong passwords, manage app permissions, and navigate the complexities of mobile security with confidence.
Whether you use an Android or iPhone, the risk of being targeted by hackers is real. From sophisticated malware and phishing attacks to exploiting vulnerabilities in operating systems, the methods employed by hackers are constantly evolving. This article will empower you with the knowledge and tools to effectively protect your phone from hackers and maintain control over your digital privacy. We’ll delve into the importance of software updates, discuss the benefits of two-factor authentication, and explain how to recognize and avoid phishing scams. By taking proactive steps and adopting a security-conscious mindset, you can significantly reduce your risk of becoming a victim of a phone hack and safeguard your valuable information.
Common Phone Hacking Techniques
Understanding how hackers target phones is crucial for implementing effective security measures. Here are some common techniques employed:
Phishing
Phishing attacks involve deceptive messages designed to trick you into revealing sensitive information like passwords or credit card details. These messages can arrive via SMS, email, or messaging apps, often disguised as legitimate communications from banks or other trusted organizations.
Malicious Apps
Downloading apps from untrusted sources can expose your phone to malware. These malicious apps can steal your data, monitor your activity, or even take control of your device. Always stick to official app stores.
Exploiting Vulnerabilities
Hackers can exploit software vulnerabilities in your phone’s operating system or apps to gain unauthorized access. Keeping your software updated is vital to patching these security flaws.
Wi-Fi Eavesdropping
Connecting to unsecured public Wi-Fi networks can make your data vulnerable to interception by hackers. Use a VPN on public Wi-Fi to encrypt your internet traffic.
Update OS and Apps Frequently

One of the most effective ways to safeguard your phone from hackers is to keep your operating system (OS) and applications up-to-date. Software updates frequently include critical security patches that address known vulnerabilities exploited by hackers.
When you delay or ignore these updates, you leave your device susceptible to attacks. Hackers often target these known weaknesses, and outdated software provides an easy entry point. By promptly installing updates, you close these security gaps and significantly reduce your risk.
Most modern smartphones allow for automatic updates. Enabling this feature ensures you receive and install the latest security patches without manual intervention. Regularly check your settings to confirm automatic updates are enabled for both the OS and individual apps.
Avoid Public Wi-Fi or Use VPN
Public Wi-Fi hotspots are often unsecured. This means that data transmitted over the network can be intercepted by malicious actors. Avoid using public Wi-Fi for sensitive activities like online banking or accessing personal accounts.
If you must use public Wi-Fi, a Virtual Private Network (VPN) is highly recommended. A VPN encrypts your internet traffic, creating a secure connection even on an unsecured network. This added layer of security makes it significantly more difficult for hackers to intercept your data.
Choosing a reputable VPN provider is crucial for effective protection. Research different VPNs and select one with strong encryption protocols and a proven track record of security. Using a VPN will significantly reduce your risk when connected to public Wi-Fi.
Enable Biometric Locks
Biometric authentication adds an extra layer of security to your device. It uses unique physical characteristics, like your fingerprint or facial features, to verify your identity.
Enabling biometric locks makes it significantly harder for unauthorized individuals to access your device. Even if someone obtains your password or PIN, they won’t be able to bypass the biometric lock without your physical presence.
Most modern smartphones support several types of biometric authentication:
- Fingerprint Scanners: This common method utilizes a sensor to read your unique fingerprint.
- Facial Recognition: This technology uses your phone’s camera to scan and identify your facial features.
- Iris Scanning: Although less common, iris scanning offers a highly secure form of biometric authentication by scanning the unique patterns in your iris.
To enable biometric locks, navigate to your device’s security settings. Look for options labeled “Biometrics and Security,” “Lock Screen Security,” or similar. From there, you can choose your preferred biometric method and follow the on-screen instructions to enroll your biometric data.
Be Cautious of App Permissions
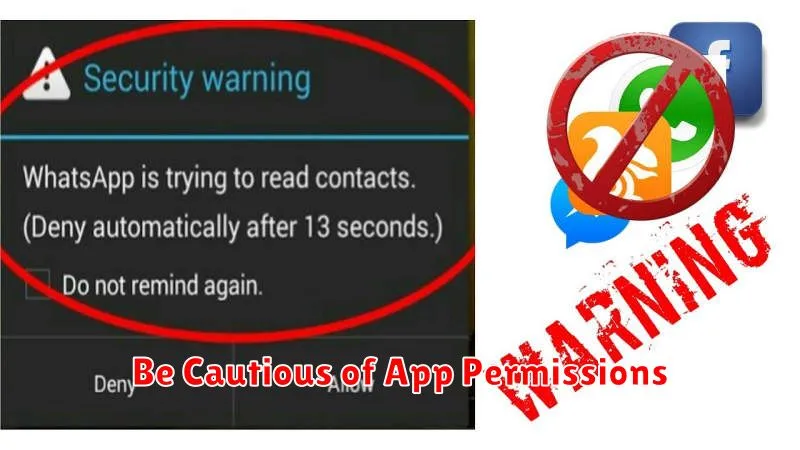
Mobile applications often request various permissions to access features and data on your phone. It’s crucial to carefully review these permissions before granting them. Overly permissive apps can potentially compromise your privacy and security.
Ask yourself if the requested permissions are genuinely necessary for the app’s functionality. Does a flashlight app really need access to your contacts? Does a game need your location? If the requested permissions seem excessive or unrelated to the app’s purpose, it’s a red flag.
Limit app permissions to only what is absolutely essential. Many operating systems now allow you to grant or deny permissions individually. Take advantage of this granular control to minimize potential risks. Regularly review the permissions granted to installed apps and revoke any that are no longer needed.
Don’t Click Unknown Links
One of the most common ways hackers gain access to your phone is through phishing attacks. These attacks often involve enticing users to click on malicious links disguised as legitimate ones. These links can be delivered via text message, email, or social media.
Clicking on an unknown link can have several negative consequences. It could lead to the installation of malware on your device, which can steal your personal information, monitor your activity, or even take control of your phone. It could also direct you to a fake website designed to collect your login credentials or other sensitive data.
Exercise extreme caution when dealing with links from unknown or untrusted sources. If you are unsure about a link’s legitimacy, it’s always best to err on the side of caution and avoid clicking it altogether.
Use Security Apps or Services
Leveraging security apps and services can significantly enhance your phone’s protection against cyber threats. These tools offer a range of features designed to safeguard your data and privacy.
Antivirus Software
Antivirus apps scan for and remove malicious software, including viruses, spyware, and trojans. They often include real-time protection, monitoring downloads and app installations to prevent infections. Regularly updating these apps ensures they can detect the latest threats.
VPN Services
Virtual Private Networks (VPNs) encrypt your internet connection, masking your IP address and online activity. This is particularly useful when connected to public Wi-Fi networks, making it harder for hackers to intercept your data. Choose a reputable VPN provider that prioritizes security and privacy.
Device Tracking and Remote Wipe
Many security suites include features to locate a lost or stolen device. Some allow you to remotely lock or wipe the device, protecting your data from unauthorized access. Activating these features beforehand is crucial for effective use.

